A few days ago, I went to Plasa Telkom in my city. I didn't intend to pay my account bill, because I've paid it, but to get free internet browsing. Shortly, my flash disk got infected by Fisika.exe Virus from the computer.
This kind of computer virus uses media of Naruto.exe file. The file name is so famous and may be, my younger brother was curious about the file. So, he double-clicked that file. As the result, Windows Media Player started and played a wmv file. The file name is naruto.wmv with 0 kb size. Ofcourse, it is a cheat file.
The other effects of this virus was occured in my system. The text "Start" on the Taskbar changed into "Fisika". If we execute Internet browser like Firefox, the title changed into "Fisika" as well. If we type "f" in Word, notepad, Location Bar of Firefox, etc., the window of the application will be minimized automatically. Although this kind of computer virus is not categorized as dangerous virus, virus is virus. It is annoying isn't it?
Besides that, the Fisika virus gets its forth by blocking registry editor, task manager and System Configuration Utility (msconfig). This virus can't be decected by many famous Antivirus software.
After trial and error, searching again and again, I was attempted to download the Final Version of ANTV-MD5-Pattern With Editor Database 5.05e. At first, this virus was not detected by this antivirus. But I tried: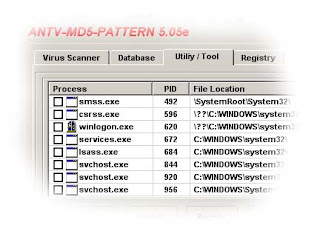 1. Select "Utility / Tool" tab.
1. Select "Utility / Tool" tab.
2. Look for "fisika.exe" from the Process list (in the infected computer).
3. Right click.
4. Select "Send to database as virus".
5. Click "Yes".
6. Scan the infected drive or folder.
Alhamdu lillah, with these steps, now, my computer is free from Fisika.exe virus.
You can download the Final Version of ANTV-MD5-Pattern With Editor Database 5.05e here.
Tuesday, June 3, 2008
How To Get Rid Of Fisika.exe Virus
Monday, May 5, 2008
N-in-1 Card Readers
 Flash memory cards have become mainstream. Practically digital cameras, PDAs and higher end cellphones all use them. It is the ubiquitous removable media standard in gadgets. However, as the old saying goes: the nice thing about standards is that there are so many to choose from. We have CompactFlash, Secure Digital, MultimediaCard, SmartMedia and more. With so many standards in the market, there emerges the need of multi card readers, or commonly marketed as the n-in-1 card readers.
Flash memory cards have become mainstream. Practically digital cameras, PDAs and higher end cellphones all use them. It is the ubiquitous removable media standard in gadgets. However, as the old saying goes: the nice thing about standards is that there are so many to choose from. We have CompactFlash, Secure Digital, MultimediaCard, SmartMedia and more. With so many standards in the market, there emerges the need of multi card readers, or commonly marketed as the n-in-1 card readers.
At first there were 4-in-1 card readers which has four slots for CompactFlash, SecureDigital/MultimediaCard, SmartMedia and MemoryStick. The 4-in-1 name seemed to be clever marketing at that time. It told people that with this reader, it was not required to buy separate reader for each kind of flash memory.
However the marketing people then realized that SecureDigital is different from the MultimediaCard, only both share the same slot. Then to their advantage, they bumped up the number and we had the 5-in-1 card readers. The 5-in-1 readers sold better than its 4-in-1 counterparts, despite the fact that they are the exact same hardware.
And so the n-in-1 arm race began.
Once again, the marketing people realized that there are two different standards of CompactFlash, the CompactFlash I and II. And there is a distinctive kind of card too: the Microdrives, even if it is technically a CompactFlash II card. The only difference is the storage media, Microdrives use metal platters similar to hard drives while traditional CompactFlashes use flash memory. So, they count all of them as separate and we had the 7-in-1 card readers (and 6-in-1 readers for those who didn’t count CompactFlash I & II as separate).
Then the xD Picture Card became standard in Fuji and Olympus cameras. For now they accepted the fact that they need to make engineering changes to accomodate this new type of memory card. Thus the 8-in-1 card readers were born.
The situation with Sony MemorySticks is even more interesting. At first there were the original MemorySticks which only support 128MB maximum memory. The short term solution to this memory limitation was to introduce the MemoryStick Select which basically two MemorySticks in one package. The long term solution was the MemoryStick Pro but it is incompatible to older devices. Then Sony introduced the MemoryStick Duo to cater the need of smaller cell phones. Like the original MemoryStick, the MS Duo is limited to 128MB of memory. The more than 128MB version of MS Duo is called the MemoryStick Pro Duo.
Sony also introduced the DRM technology to its MemorySticks armada. The products with DRM technology are marketed with ‘MagicGate’ suffix, and so marketing people recognized them as different products, especially when there are products without the MagicGate label. These are the MemoryStick MagicGate, MemoryStick Select MagicGate, and the MemoryStick Duo MagicGate.
OK, now I’ve lost count. What is it? 15-in-1? They even bumped up the number even though to use the smaller MemoryStick Duo, users will need to use a special adapter.
The SecureDigital and MultiMedia Card were also evolving. For SD, the result are the smaller miniSecureDigital (miniSD) and the even smaller microSD which also known as the Sandisk Trans-Flash cards. For MMC, the result are the MultiMediaCard II and the Reduced-Size MultiMedia Card (RS-MMC). Of course they bumped up the number even though the smaller cards will require a special adapter if to be used with card readers.
Now we are at 19-in-1. To make the number even, one manufacturer even counted the Sandisk brand name MemoryStick Pro Ultra II. So, we now have the 20-in-1 card readers. 20-in-1 Card Reader But, what are the differences between the original 4-in-1 and the current 20-in-1 card readers? Not much, apart from:
20-in-1 Card Reader But, what are the differences between the original 4-in-1 and the current 20-in-1 card readers? Not much, apart from:
- support for xD Picture Cards
- support for the MemoryStick Pro
- support for smaller variant of cards in a few readers
Monday, April 28, 2008
Upgrade to Vista: Yes or Not
With all of the new features of Windows Vista, there’ll be a mighty temptation for you to buy a copy of the operating system in a store and immediately install it over your existing instance of Windows XP, 2000, Me, or 98.
Before you do, you should consider some of the following cautions:
Your old PC may not be up to the challenge of running Vista. You may need substantial investments in additional RAM, a more capable video card, a larger hard drive, or all of the above to get adequate performance from Vista.
Some of your hardware, such as printers and networking adapters, may not work at all after you install Vista—unless you update the drivers they need to versions that are Vista-compatible.
Even if you find that one or more of your drivers needs to be updated, the vendor of your hardware may not make a Vista-compatible version available for months, years, or ever. (It’s happened before with previous versions of Windows.)
We do recommend that you get Windows Vista preinstalled when you’re buying a new PC. But you may be surprised to learn that we don’t recommend that you install Vista over XP or an older version of Windows.
The reason is that installing Vista on top of another version of Windows may cause incompatibility problems that you might not be able to easily fix. When you buy a PC with Vista preinstalled, it’s almost certain that the components in the PC will have been selected for their compatibility and will have the latest driver software. If you install Vista to an older machine yourself, however, you may find that your printer, networking adapter, or some other vital component no longer works because the version you have of its driver is incompatible.
In general, you shouldn’t consider installing Vista over an older version of Windows unless the following conditions are true:
• You need a feature of Vista that you can’t add to XP; or
• You need an application that requires Vista; and
• You can’t afford even the least expensive new PC that comes with Vista preinstalled
Even if one of the above cases is true, you may be better off burning your old data to a CD, formatting the old PC’s hard drive, and doing a clean install of Vista. This avoids the possibility that some components of the old OS will hang around to cause conflicts.
If you’ve never before backed up and formatted a hard drive, however, don’t try to learn how on any PC that’s important to you.
by: articolando
Sunday, April 27, 2008
Recover File and Recover Data Tools
The latest innovations in the computer field may prompt people to sell their old computers to buy new and the latest model computers. When selling the old computers, one normally deletes all the files on the computer, re-install the operating system and sometimes also format their drive so that all the files and data found in the computer does not fall in the wrong hands.
However seldom are they aware of the fact that their personal and private information may still remain on the disk in an unallocated space. It is only with the help of a data shredder software is it possible to get rid of all pictures, data and information permanently from the computer.
It is very important to get rid of all sorts of data fragments that may be present in the computer with the use of data shredder software. This is because if you venture to sell or discard your old computer without getting rid of all the data in the computer may only lead to irreparable, financial, political and personal damage to the owner or organization of the computer. There is a chance of this personal and confidential information falling into the hands of terrorists, pedophiles and also a possibility of the owner of the computer getting blackmailed or threatened, if it reaches the hands of hackers.
The best thing to do to get rid of all types of information permanently is with the help of some data shredder software. This software can be bought for a fee on the internet and can also be accessed from the internet for free. All you have to do is to visit the data shredder software site and pay for the software wherein you will be able to download the software to your computer. With this software installed, you are sure that all the information that you want to be eliminated from the computer is genuinely deleted.
Most of the data shredder software not only helps in shredding data from the computer, but also helps in data recovery. This is an important part of the data shredder software as many a time a file that was not supposed to have been deleted may get deleted. In such cases, there will be a need of recovering the file that was accidentally or intentionally deleted. So it can be seen that it is very important for all computer owners to have some type of data shredder software installed in the computer at all times.
by: samroberts
COMPUTER VIRUSES: Making The Time Fit The Crime
The computer virus may just be the modern plague that afflicts the upcoming millennium. The "infection" numbers are staggering. The annual damage cost associated with viruses was estimated at over $1 billion for last year and is expected to rise to $2 to $3 billion in the upcoming year. One survey found that 98 percent of North American businesses have been infected by the over 6,000 types of viruses that are currently cataloged. One virus, Concept, is believed to have infected nearly one half of all companies nationwide within one year.
While once seen as pranks or the products of misdirected creativity, viruses now comprise business pathogens with destructive powers. In light of the tremendous and growing costs of computer crime, which spiral upward as more businesses link to the Internet thus accelerating the rate at which contagion can spread, the FBI's Computer Crime Squad in late January mounted a nationwide series of raids targeting the seizure of evidence of various computer crimes, including the spreading of viruses.
---------------------------------------------
---------------------------------------------
Today, in the U.S., the most likely avenue of prosecution is the Federal Computer Abuse Act of 1994 (18 U.S.C. Sec. 1030). Amending the earlier 1986 Computer Fraud and Abuse Act, the new Act is much clearer and more encompassing than the older act.
Seeking to avoid hypertechnical arguments about what is and is not a "virus" -- or a "worm" or a "Trojan horse," etc. and whether they differ from "viruses" -- the new Act outlaws the "transmission of a program, information, code, or command" that "cause[s] damage to a computer, computer system, network, information, data or program." 18 U.S.C. Sec. 1030(a)(5)(A). As intended, this language should encompass both existing viruses and any future virus-like creations. The earlier law, which focused on the unauthorized access to a computer system, proved to be ineffectual at times because it focused merely on the crossing of a system-level boundary and also became outdated as technology advanced. The new law is an improvement because it's directed against the act of transmitting the virus. Prosecutors are no longer strained to argue that the viral release constitutes an unauthorized entry, instead the deliberate transmission of a viral release is a crime unto itself.
The 1994 Computer Abuse Act tries to deal differently with those who foolhaeartedly launch viral attacks and those who do so intending to wreak havoc. To do this, the the Act defines two levels of prosecution for those who create viruses.
For those who intentionally cause damage by transmitting a virus, the punishment can amount to ten years in federal prison, plus a fine.
For those who transmit a virus with only "reckless disregard" to the damage it will cause, the maximum punishment stops at a fine and a year in prison.
By differentiating along the lines of the intent to damage, the new law efficiently accounts for the two typical "strains" of viral creators. The first "strain", which is becoming increasingly more common, is the intelligent, disgruntled employee or contractor or sociopath who intentionally infects someone's computer system so as to destroy data and files. Recent cases of this type have appeared in New York, Texas, Illinois, and Wisconsin. Under the new federal law, these individuals would be classified at the "intentional" level and thus could face up to ten years in prison.
The second classification deals with what we more would commonly perceive as the stereotypical viral creator -- typically, a young computer wiz who is both curious and eager to show off his or her expertise by pointing out the flaws in the "system" or in the computer safeguards erected by others. The case of the 1988 "Internet Worm," that Robert Morris, Jr. incubated and released, typifies this kind of criminal defendant. According to Morris, he launched his "worm" to point out the security flaws of other computer networks. However, his worm program replicated much faster than Morris expected and caused over a billion dollars in damage by overloading systems and causing them to crash or slow to the point that they became non-functional.
The U.S. Justice Department prosecuted Morris under the 1986 Act, an awkwardly worded piece of legislation arguably unclear as to the necessity that the prosecutors prove Morris had the specific intent to cause damage. Morris argued that the damage he caused was unintentional and, thus, his action not illegal under the old act. The case went to the United States Court of Appeals for the Second Circuit, which upheld Morris' conviction and held that there was no intent-to-cause-damages requirement. United States v. Morris, 928 F.2d 504, 509 (2d Cir.), cert. denied, 502 U.S. 817 (1991). However, in our federal legal system, the decisions of the Second Circuit technically do not "bind" the numerous federal district courts sitting in other circuits, the possibility existed that other appellate courts might rule differently, and the "intent" issue might pose a potential "defense" for others who launched viral attacks until the U.S. Supreme Court decided the question. While Morris' conviction and sentence to three years' probation and a $10,000 fine made national headlines and were upheld, the case highlighted the difficulty of prosecuting a viral creator who does not necessarily intend the disasterous consequences wrought by the infectious spread of his creation.
Congress' response of creating a standard of "reckless disregard" makes it both easier to prosecute cases like Morris and easier for prosecutors to determine if the act of creating a virus is chargeable. The 1994 Act makes clear that the creator of a virus cannot hide behind the cloak that he did not really mean to hurt anyone, or that he really only wanted to send a message or, as in Morris' case, point out a flaw. While the courts may need to evaluate what qualifies as "damage" to a computer or computer system, as the new Act uses those terms, it seems that any interruption in service, which in turn causes a disruption in business, will likely fulfill the requisite damage component.
Under the new Act, a software genius who foolheartedly creates a "benign" virus that does not actually cause a computer to crash can still be prosecuted (if the damage is at least $1,000 in the aggregate), although the maximum punishment is less than that to be levied upon the maker of a "malignant" virus who intentionally aims at destroying files or data. The new law constitutes a much more responsible approach to the growing problem of computer viruses. By specifically not defining a virus, and rather describing the act, the drafters have left it open to cover the next wave of technological attacks on information systems, whatever form that may take. In differentiating the levels of offense, the new law lines up more closely with the commonly held beliefs of what is criminal. Clearly society would see fit to more severely punish someone who attacks another's computer based on a grudge or the sheer delight in creating havoc than someone who causes the destruction of computer services due to a failure to recognize the consequences of an attempt to "show off" one's expertise. Although some degree of variation for the punishments seem fitting, it hardly seems likely that even the less culpable miscreant in these examples should get off without any punishment in light of the extreme costs that such behavior can cause.
While some have continued to debate whether the penalties are too severe or too mild, the reality of the situation is that it will take some time for judges, prosecutors and society to find a comfortable level of punishment. Yet as the costs of such behavior rise, society may find itself willing to provide harsher punishment. One example comes from England where after the judge sentenced that nation's first convicted virus creator to 18 months imprisonment, the judge stated, "Those who seek to reap mindless havoc on one of the vital tools of our age cannot expect lenient treatment." Undoubtedly, business, which faces most of these costs first-hand, will be in the forefront of any effort to increase the penalties in order to provide some degree of deterrence to such a costly activity.
Joseph N. Froehlich, Edward M. Pinter, and John J. Witmeyer III
Ford Marrin Esposito Witmeyer & Gleser, L.L.P.